A Conversation on Cryptography, Trust Machine, and Cyber Planet Construction
Subtitle: SciEcon AMA with Prof. Director. Kevin Mo at Blockchain and Privacy-Preserving Computer Research Center, Beijing Big Data Research Institutes.
About Prof. Kevin Mo:
Figure 1: Prof. Kevin Mo
Introduction to Prof. Kevin Mo:
Professor Kevin (Xiaokang) Mo is the Director of Blockchain and Privacy-Preserving Computation Center, Beijing Big Data Research Institute, which is affiliated with Peking University. He had his Ph.D. in mathematics from Stanford University and had years of experience working in the field of quantitative financial modeling. In recent years, he has been focusing on the study of blockchain and privacy-preserving computation. In 2020, he was invited by Professor Shing-Tung Yau to be a Distinguished Research Professor at Beijing Institute of Mathematical Sciences and Applications, and a Visiting Professor at Yau Mathematical Sciences Center, Tsinghua University. He is an Editorial Board Member of the Journal of Blockchain Research. He also participated in some joint international research projects in the field of zero-knowledge proof, focusing on PLONK and Plookup, which was initiated by Luke Pearson from Dusk Foundation, and contributed to the improvement of some algorithms.
Watch our AMA interview for Prof. Kevin Mo on our YouTube channel, SciEcon.
Read the Interview Scripts with annotations and citations.
Opening Remarks
Prof. Luyao Zhang:
Hi everyone! Today we are very honored to have Professor and Director Kevin Mo here, for SciEcon AMA. Today, we will discuss the conversation on Cryptography, Trust Machine, and the Cyber Planet Construction. Thank you so much for being here with us, Kevin Mo.
Prof. Kevin Mo:
Thank you!
Question 1
Prof. Luyao Zhang:
We know that you are the Director of Blockchain and Privacy-Preserving Computation Center, Beijing Big Data Research Institute. What is your motivation for doing research in the fields of blockchain and privacy-preserving computation?
Prof. Kevin Mo:
I would like to answer this question by drawing a parallel between the physical world and the cyber world.
Humanity as a species has been living in the physical world throughout its long evolution history tracing back to the time when life was born on earth. Great amounts of accumulated experiences and knowledge gradually developed into systematic scientific theories such as Newtonian mechanics [1], Einstein’s relativity [2], quantum physics [3], and so on, which attempted to capture the natural laws of the physical world. The understanding of these natural laws made it possible for human beings to observe and manipulate elements of the physical world, namely various forms of matter and energy, with great precision and accuracy. This became the foundation of technological developments such as the invention of automobiles, airplanes, satellites, semiconductors, lasers, GPS, and so on, which provided much comfort and convenience to humans living in the physical world.
Since the inception of business Internet in 1994 (Charmonman et al, 1994), humanity has started a process of rapid migration from the physical world to this newly created cyber world, which has been growing every day, and becoming more and more like our second home. This cyber world is similar to the physical world in the sense that both are kind of “places” where we can “live in”, namely, to conduct various activities, to interact with each other, and to enjoy. On the other hand, the cyber world is also very different from the physical world, with its own peculiar properties. It has its own natural laws, and therefore must have its own sciences and corresponding technologies. What are they?
My personal answer is: the so-called “privacy-preserving computation”, in its theoretical aspect, namely the science of advanced cryptography, is nothing but the science of the cyber world. It began with Diffie and Hellman’s groundbreaking paper in 1976, and now includes things like zero-knowledge proofs [5], homomorphic encryption [6], secure multi-party computation [7], and so on. It is the result of many important scientific discoveries (comparable to Einstein’s discovery of relativity) made in the past 45 years or so, capturing fundamental natural laws of cyberspace [4]. These natural laws are quite subtle and intricate, often counterintuitive, in the sense that many seemingly impossible things are shown to be possible. They are more abstract than Newton’s gravity, not so easy to grasp without some mathematical thinking.
Figure 2: Zero-Knowledge Proofs
Along with the scientific exploration, technological development of the cyber world takes form around 1995 when SSL/TLS was developed in Netscape Navigator. This PKI/HTTPS technology [8] was the first attempt to bring some order to the new cyber world, which made e-commerce possible. But the true milestone was the invention of the blockchain (Nakamoto, 2009), which for the first time demonstrated the possibility of constructing a self-governing “civilized cybercity”, which seems entirely independent of the physical world.
We summarize the above in the following formulas:
privacy-preserving computation = science of cyberspace
blockchain = technology of cyberspace (in today’s form)
Figure 3: Visualization of Science and Technology of Cyberspace
Question 2
Tianyu Wu:
We all know the importance of the Internet and cyberspace as you put it. But this really involves the whole field of “computer science”, right? Why do you give special importance to privacy-preserving computation and blockchain technology?
Prof. Kevin Mo:
Yes, this brings us to the central point of the matter, which is TRUST construction.
In my view, cyberspace today as a whole is still like the planet Mars, not quite ready for human habitation. Great ecological transformation is needed to make it a truly livable planet. The central factor of this transformation is the formation of an overall ground of TRUST, upon which other social and economic constructions can be built. The blockchain revolution that started in 2009 was a major breakthrough in this direction. But much more is still needed.
In the physical world, civilized human living requires stable supplies of food, shelter, clothing, and basic social structure such as families, tribes, or more advanced forms of social governance, which provides the basic sense of security. In the case of cyberspace, a similar sense of security is also needed, so that its inhabitants can interact with each other in trust and confidence. Trust in cyberspace is as basic as food and shelter in the physical world.
To come back to your question, my answer can be summarized as follow:
privacy-preserving computation = science of trust
blockchain = technology of trust (in today’s form)
Figure 4: Visualization of Science and Technology of Trust
We add the qualification “in today’s form” because there is the feeling that blockchain technology is likely to evolve into some much more sophisticated form in the future and may not be called “blockchain” anymore.
Figure 5: Cybertrust
Now, what do we mean by trust? Roughly speaking, in a multiparty cooperative mechanism, trust means the confidence that everything will happen only within pre-defined rules. More precisely, every party can “do things” and “know things” only within those rules. To get a more concrete idea, just imagine four persons playing a game of bridge. A set of rules specifies what each party can do and can know. So, we have the following formula:
Trust = Proper Behavior Enforcement + Privacy
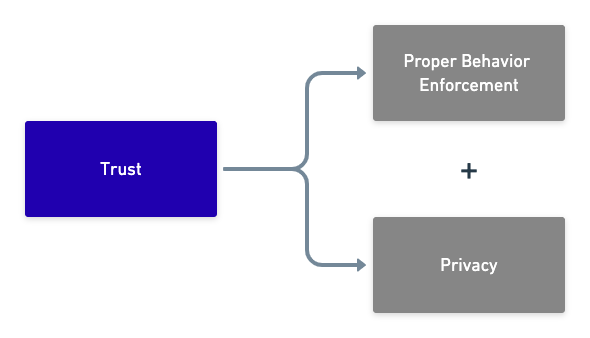
Figure 6: Trust
which captures the two fundamental aspects of trust. In this view, we realize that the term privacy-preserving computation is partial in its meaning. A more accurate terminology should be:
Trust Computation = Theory of Advanced Cryptography
Trust Engineering = Blockchain (and Its Future Variants)
Figure 7: Trust Computation and Trust Engineering
Question 3
Xinyu Tian:
From your description above, you seem to imply that the construction of trust in cyberspace is not a small task, and we are still in the beginning stage of this work. If this is the case, could you elaborate further, so that we get a more concrete idea of what you mean by trust construction, and also an overall picture of what lies in the future?
Prof. Kevin Mo:
Yes, I do think trust construction in cyberspace is essentially the building of entirely new infrastructure. In terms of the time period, it would be reasonable to think on a scale of say 30–50 years. We can compare it with the building of the Internet, which is essentially an infrastructure of connectivity. It has been going on for nearly 30 years by now, and we cannot quite say it has reached its full maturity. But as we will see more clearly along with our discussion, “trust” is something much more complex and sophisticated than “connectivity”. So we cannot expect it to be done very quickly.
Now, let’s try to understand the matter from a historic perspective and see how the science of cryptography helps to build step by step an increasingly more powerful trust infrastructure for human society. For the sake of explanation, I will divide it into four development stages.
Trust 1.0: Symmetric Cryptography
This goes back to the time of Julius Caesar [9] (or even earlier) and reached a high degree of maturity in the 1970s when the Data Encryption Standard (DES) was published. It was a technology of secure communication that represented the first step of trust construction for human interaction in the “information space”. There was no cyberspace as we understand today, but you can also think there was a kind of cyberspace in its infancy. One thing to realize is that it has taken humanity 2000 years to reach this stage. Even if we count from the beginning of the 20th century, it has still taken decades of time to mature the technology. In this case, maturity means, first of all, that the encryption is practically unbreakable in a strong enough sense.
Figure 8: Symmetric Cryptography
Trust 2.0: Public-Key Cryptography, PKI/HTTPS
Public-key cryptography was discovered around 1976 (Diffie and Hellman, 1976), which opened entirely new possibilities. 20 years later, around 1995, it was used in the design of SSL/TLS[10] in the HTTPS protocol. Together with the hierarchy of PKI (public-key infrastructure), a certain trust system was established, so that general e-commerce became possible. Individuals and institutions were confident enough to input their private information on a web page for business transactions.
Figure 9: Public-Key Cryptography
Nowadays, HTTPS and e-commerce have become so commonplace, so we forgot that this had been a great technical achievement, which would not be possible without its scientific foundation (public-key cryptography). This was the first step of bringing trust to cyberspace. But this approach still depends heavily on the existing trust system of the physical world. It also followed the traditional logic of relying on some third-party authorities.
Trust 3.0: Nakamoto’s Blockchain, Half Trust Machine
Satoshi Nakamoto’s Bitcoin in 2009 brought an entirely new conception of trust to human society. It effectively constructed an intrinsic trust system within cyberspace itself, with almost no reference to the physical world. Cooperative parties can deal with each other without know the other party’s physical identity or other physical attributes and conditions. Blockchain is then also called a TRUST MACHINE.
What exactly is a trust machine? Nakamoto’s original vision is clear. The main purpose is to be free of the traditional reliance on “trust third party” (TTP) [11]. Through a distributed protocol based on cryptography (plus some economic principles), one effectively creates a “virtual TTP” which functions almost like a real TTP. This is to say, Bitcoin functions almost like a real bank, without having such a bank. This is the meaning of the trust machine. A trusted machine is nothing but a set of distributed computer programs that collectively function almost like a TTP, without actually having that TTP.
But things are not so simple yet. Does Bitcoin truly function as a real bank? The answer is “not quite”, and there is some vital difference. A real bank maintains strict privacy for its customers, while Bitcoin simply doesn’t have that ability. All accounting information of Bitcoin is open to the public.
Nakamoto was clearly aware of this weakness and suggested a few remedies in the latter part of his original 2008 paper, which was not a real solution at all. But Bitcoin has been functioning fine so far despite this weakness. This is largely because the world of Bitcoin now operates quite independently from the physical world, so that the privacy problem can be tolerated. But if you want to use blockchain in real-world business applications, this will not work anymore. Real business data is almost always highly confidential.
The above analysis is leading to an important conclusion. Nakamoto’s blockchain is not yet a “trust machine”, so we call it a “half trust machine”. As such, it is incapable of delivering most of its promises to society under the vague idea of a “trust machine”. You might ask, who made those promises? Maybe nobody in particular, but there was just a huge collectively created misunderstanding. To put this issue in focus, let’s just look at one business use case: to build a fully decentralized stock exchange which can replace NYSE and NASDAQ, in which quotations from traders are strictly confidential information. Careful examination of this case should convince you that Nakamoto’s blockchain is incapable of this task. More generally speaking, Nakamoto’s blockchain is mostly unusable for real business applications.
Is there a solution to the above problem? To answer this question is really the central theme of our conversation.
Figure 10: Bitcoin
Trust 4.0: Trust Computation, Full Trust Machine
Seeing the inadequacy of blockchain as a “half trust machine”, is there such a thing in the world that can be called a “full trust machine”? One may be surprised to learn that such a trust machine has been discovered long ago before blockchain. The prototype of which was given in Shamir, Rivest, and Adleman’s 1979 paper: Mental Poker, (the same authors discovered the famous RSA algorithm in 1978). The paper raised a very strange question: Can two potentially dishonest players play a fair game of poker using no cards (e.g. over the phone)? Hearing such a question, almost everybody should answer “impossible”. But contrary to your expectation, the paper provided a positive solution. Think about this more carefully. You may realize how peculiar and how amazing this is.
Figure 11: Trust Machine
I personally regard this as a great scientific discovery of information science. Using today’s concepts, this may be thought of as a fundamental discovery about cyberspace, comparable to Newton’s discovery of gravity about the physical world. This was 30 years ahead of blockchain, and from scientific point of view, a far superior achievement than blockchain. It accomplished something that the blockchain is incapable of, namely the formation of mutual trust in full privacy.
To be more precise, it means the construction of a certain mathematical communication procedure between two persons, so that they can engage in a certain interactive game (such as poker), in which each party cannot know anything about what happens in the other party (unless allowed by the rules), and yet cheating is not possible. Because thou hast seen me, thou hast believed: blessed are they that have not seen, and yet have believed. John 20:29 [12].
The above initial discovery was studied further by Andrew Yao (1982) with the famous millionaire’s problem, which gave birth to a new branch of cryptography, secure multiparty computation (MPC). In its most general formulation, the problem MPC intends to solve is exactly the construction of a “full trust machine”, namely an interactive protocol which functions “fully” as a trusted third party (TTP). During the 1980s, the above goal had been fully achieved under very general assumptions (such as the number of adversaries is less than ½, or less than 1/3, and so on).
Figure 12: Secure Multi-Party Computation
After all the above explanation, let’s jump to a general statement: the vague vision of blockchain as trust machine, as entertained by many people in the society, the business community, or even many blockchain professionals, cannot be realized by blockchain alone. But it can be realized through advanced cryptography (alone or in combination with blockchain), which includes sophisticated schemes such as zero knowledge proofs, homomorphic encryption, secure multiparty computation, and so on. This constitutes the true promised land of trust construction in cyberspace.
Question 4
Prof. Luyao Zhang:
You distinguished “half trust machine” from “full trust machine”. Can you go further into the exact difference between the two?
Prof. Kevin Mo:
OK, let’s go into the mental poker problem in a little more detail. Consider two poker players, A in San Francisco, B in New York, and they want to play a game on phone. How would they do that? The easiest solution is to find a third person C, whom both A and B trustfully. With the help of C, A, and B can play the game easily.
Now, what do we mean by trusting C? It includes two aspects: 1) C must ensure both players follow the rules of the game; 2) C must not reveal any more information to each party than prescribed by the rule of the game.
Now, the whole point of the “mental poker problem” is to realize the above function of C through a telephone conversation between A and B, without having the actual person (or a machine) C. In other words, one must design such a special form of conversation (called a protocol) such that it emulates C’s job in both aspects: 1) rule enforcement; 2) information hiding (privacy). Blockchain can emulate the first aspect, but not the second. Blockchain can emulate chess (which contains no private information), but not poker. Let’s summarize our analysis in the following formulas:
half trust machine = phone call which can emulate chess game
full trust machine = phone call which can emulate poker game
What’s the implication of this to business? Now, consider any real-world multiparty business cooperation, would it be more like a chess game or a poker game? We have talked about the case of a fully decentralized stock exchange, which trades not a cryptocurrency, but real stocks. We can also think of the auction market, restate agency business, and so on. You can analyze dozens of business use cases, and come to realize that almost all valuable cases are more like poker rather than chess, namely that privacy is an absolute requirement.
Conclusion: blockchain without advanced cryptography is only a “half trust machine” which has only limited value in real-world business applications. The future lies in the construction of a “full trust machine” through advanced cryptography (possibly in combination with blockchain).
Question 5
Tianyu Wu:
What you said seems to make sense. But if as you said, a much more advanced and powerful theory/technology you named “trust 4.0” already existed in the 1980s, then why is there still a place for blockchain which came much later in time?
Prof. Kevin Mo:
Good question. So far, we have emphasized the vital limitation of blockchain as a “half trust machine”. But to gain a full picture of the situation, we need also to understand a few other important points.
Point 1: General Purpose “Full Trust Machine” is Not Practical Today because of High Cost
Full trust machine in its most general form has been accomplished in the 1980s in MPC theory. However, the computation/communication cost required is very high. Great improvements have been made during the past 15 years or so. But it’s still quite far from being practical.
A full trust machine could also be constructed using fully homomorphic encryption (FHE) schemes (the first such scheme was constructed by Craig Gentry’s Stanford thesis in 2009, which had been a great breakthrough in cryptography). These schemes allow arbitrary computation to be performed on encrypted data without decryption. But it also suffers a similar performance cost problem. Using the best-optimized scheme today, FHE’s computation cost is still about 1,000–10,000 times of ordinary computation.
Figure 13: Fully Homomorphic Encryption
Trust Machine is a truly revolutionary concept that can change the underlying foundation of human society, including business as well as social governance in general. However, its full realization does incur such a high cost that it’s not practical available yet.
In contrast, blockchain as a half trust machine, has the advantage of being immediately available. Acting as a kind of “toy car” technology, it allows the society at large to play with it, and get familiar with many of the new concepts involved. Bitcoin, Ethereum, DeFi, NFT, GameFi, Metaverse are among such experimentations that have been conducted at scale, without waiting for the true technology of “full trust machine”.
Point 2: Why Blockchain as a “Toy Car” Solution Is Still So Successful?
The phenomenal success of blockchain since 2009 testify to the ingenuity of its design. The idea of replacing TTP with a distributed protocol is expressly stated in Nakamoto’s paper. But unlike MPC theory which tackled the problem in its full generality, Bitcoin focused only on one simple case: electronic cash payment system, which simplifies the problem greatly. Let’s look into a number of factors which contributed to its success.
1) By focusing on the payment system, it needs to deal only with simple mathematics of addition and subtraction mostly. This made the system very light.
2) Nakamoto left the problem of privacy unsolved. Bitcoin (and other cryptocurrencies) practically got away with this problem by the fact that users’ crypto identities (their public keys and private keys) are not linked to their physical identity.
3) Blockchain introduced an economical (or game-theoretical) principle into the protocol. So, its security depends not only on cryptography, but also on the economic interests of the participants. In other words, to attack the system may not be in their best business interests. This is indeed a new contribution made by blockchain design.
4) It created and issued new “currency” out of nothing, which practically caused a continuous flow of transition of wealth from society in general to the crypto community. It may sound a bit like robbery, but we will not get into moral issues here. In any case, it provides a powerful channel of financing to the community so that continuous innovation, development, and system maintenance are well supported.
All these contributed to the quick rise of blockchain. The vital issue of privacy has largely been evaded, but not resolved. It will prevent blockchain from going very far into real-world business applications.
Question 6
Xinyu Tian:
You have just described two cases: on the one hand is the general-purpose full trust machine, which is good in theory but impractical due to the high cost. On the other hand, is blockchain as a half trust machine that cannot maintain privacy, and therefore not good enough for business use. So, what is the way out?
Prof. Kevin Mo:
Interestingly, besides the two extreme cases, there seems to be a vast promised land in between. One particularly interesting approach is the combination of blockchain with zero-knowledge proofs.
To appreciate the value of this approach, let’s look into another vital defect of the original blockchain design: the extreme inefficiency of the system due to the requirement that every miner must repeat all the work of bookkeeping. As a result, blockchain’s computation and storage capacities are extremely limited. These fundamental difficulties are also expressed as Vitalik’s blockchain trilemma among decentralization, security, and scalability.
As it turned out, Zero Knowledge Proof (ZKP) proves to be a powerful tool to solve these problems. Simply put, both the privacy problem and the efficiency problem.
Historically speaking, Nakamoto’s Bitcoin paper in 2008 was preceded by a series of sophisticated research in e-cash, in which the ideas of using ZKP had been explored extensively. Bitcoin did not use any of it, but the ideas were around in the circle. An important development was the appearance of the Pinocchio protocol in 2013, which for the first time brought the performance of general-purpose ZKP to a practical level. This was then implemented in Zcash and launched in 2016, which demonstrated the power of ZKP in facilitating mutual trust in full privacy.
After Zcash, some other different cases were developed, each demonstrating the power of ZKP from a different angle. Together they seem to indicate a very promising direction for the near future. The following are some of the interesting cases:
1. The transition from Proof-of-Work (PoW) [13] to Proof-of-Stake [14] through the use of Verifiable Random Function (VRF) [15] which has in it the element of ZKP, and we see this in the research of Algorand, Ouroboros, DFINITY and Dusk Network.
2. Ethereum scalability through zk-rollup, which expands the computation and storage capacity of the main chain by delegating those tasks to off-chain resources, while ensuring the correctness of those computations through ZKP.
3. Dusk Network expands on Zcash and aims to support real-world security trading (going outside the crypto world), in which privacy is a requirement, not an option.
4. FileCoin uses Verifiable Delay Functions (VDF) (Boneh et al, 2019) and Proof-of-Storage (PoS) [16]. We see ZKP in the role of creating trust among different parties so that they can work together in coordination to form a single larger system.
5. Mina uses a sophisticated form of ZKP called “recursive proof” (Bowe et al, 2019) to achieve something quite amazing. It manages to compress the whole blockchain into the size of 22k, so that even a very light node (say an old mobile phone) can participate in the process of verification. This technology may be used to prevent the situation as in for example Bitcoin where power got more and more concentrated in a small number of mining pools.
6. zkEVM represents a more recent effort to provide a comprehensive solution in this general direction. Some time is still needed for us to see how successful it may be.
In summary, this approach aims to develop a blockchain system which can fully satisfy the two major demands of real-world business applications: 1) absolute privacy; 2) reasonable level of performance. Viewing as a trust machine, it lies in the middle ground between the two extreme cases as you asked.
Question 7
Prof. Luyao Zhang:
It’s exciting to hear about all the progress with this approach of combining blockchain with ZKP. How would you put it in the bigger picture of trust machine construction?
Prof. Kevin Mo:
As discussed earlier, a general purpose “full trust machine”, which fully emulates an all-powerful TTP, is the ideal technology that lies at the heart of the vision of decentralization. However, this ideal technology exists only in theory today. Even with the best-optimized algorithms, the best available commercial hardware, and the best attainable network speed, its implementation would still be too slow. So, this technology is not quite ready yet for large-scale adoption by the industry.
The blockchain + ZKP approach is different. It is fast enough to be usable now. Naturally, it cannot be “general purpose”. It can only handle specific class of multiparty computations. So, we may call it special purpose “full trust machine”. It is “full” in the sense of fulfilling both demands of trust, namely: 1) proper behavior enforcement; 2) privacy.
Regarding the “special purpose” aspect, how special exactly? This is something that needs to be clarified by further research. One point to be noted is, this approach seems to work well only with tasks which do not require complex computations with a lot of data mixing among different parties. But fortunately, it does cover a very wide range of valuable business applications. One can reasonably expect the gradual realization of its enormous potential in the next 20–30 years.
What about complex computations with a lot of data mixing among different parties? Again, useful computational tasks are usually not so “generic”. To the specific class of computations, specific optimization may be found. If not, then in principle, it may really require general-purpose MPC schemes, or full homomorphic encryption schemes, which are very costly. An alternative to that is the hardware solutions based on TEE [17]. It is fast enough, but then you will need to trust the hardware vendors for security.
Another approach to the privacy problem is through access control. This approach is used extensively by the so-called permissioned blockchain. But it this approach appears to have a fundamental conceptual weakness. By keeping certain data private from a certain party, also renders the data totally unusable by that party. This is not the kind of privacy we really want, because it defeats the very purpose of a trust machine. The whole point of a trust machine is to be able to use those data without seeing them. This leads us to the following view: blockchain schemes heavily based on access control seem to have deviated from the vision of the trust machine fundamentally. This deviation naturally carries over to the business application level. The power of blockchain as a disruptive technology may be lost to a very large degree. Some people may think otherwise on this point, but let time tell it.
Question 8
Tianyu Wu:
Can you briefly envision the future society in Cyberspace by highlighting some of your research interests in blockchain and cryptography?
Prof. Kevin Mo:
It has taken humanity a few thousand years to build the whole physical infrastructure on earth which is the foundation of modern civilized living, with all its comfort and convenience. A similar process of construction is also needed for the newly born cyber planet, and the very foundation of this construction is the technology of the trust machine.
The first social experiment on the trust machine is Bitcoin started in 2009. It is somewhat of a miracle that it succeeded on its first trial, with millions of users today, and a market cap of $1 trillion which ranks among the top 10 public companies in the world. Along with the growth of Bitcoin, we see an explosive development of various types of trust machine technologies. Most of them are based on either blockchain, or a combination of blockchain with something else.
It has taken humanity a few thousand years to build the whole physical infrastructure on earth which is the foundation of modern civilized living, with all its comfort and convenience. A similar process of construction is also needed for the newly born cyber planet, and the very foundation of this construction is the technology of trust machines.
The first social experiment on trust machines is Bitcoin started in 2009. It is somewhat of a miracle that it succeeded on its first trial, with millions of users today, and a market cap of $1 trillion which ranks among the top 10 public companies in the world. Along with the growth of Bitcoin, we see an explosive development of various types of trust machine technologies. Most of them are based on either blockchain, or a combination of blockchain with something else.
It is a very young age. So, we expect to see a long period when people will try many lines of development. However, I have the feeling that all these different developments will gradually merge into one Global Trust Machine, or Global Trust Infrastructure, with the following properties:
1. The Internet today as a network of connectivity will be transformed into a network of trust, on which any two strangers on earth can trust each other fully and instantly. This mutual trust is not based on moral evaluation of the other party, but rather on the powerful “trust machine technology” which makes any violation of rules practically impossible.
2. All data from all individuals and institutions on earth are shared, as if in one huge single database. These data can be used in specific ways as authorized by the data owners. These authorizations will specify what computation is allowed, and to whom the results can be given. Beyond such authorized use, all data are kept in full privacy.
3. All computers in the world owned by different individuals and institutions are connected in such a way that they together function like a huge single computer, available for use by everyone. Again, this is done with full protection of privacy for all parties.
4. The organization of human society will be changed fundamentally. Traditionally, the primary function of most human organizations is to provide trust, namely, to act as a TTP. But this function will no longer be needed when the Global Trust Infrastructure becomes widely available. The implication is: most human organizations as we know today will disappear.
5. In particular, most of the business models we know today will disappear. Business models which are based on various forms of the monopoly of resources, such as data, information, special knowledge, and other privileges will gradually lose their overwhelming dominance. The whole economical structure will take a new form in which most values are given to those activities of actual products and services. On the other hand, sales as a profession, advertisement as an industry (which makes up about 2% of GDP today), may gradually disappear.
In fact, the future is already happening now. The large-scale experimentation of DeFi since 2020 may eventually lead to the disappearance of all traditional financial institutions and the whole industry. This change will not stop with finance but will expand to the whole economy and the whole society in every aspect. This was what happened with the Internet in the past 25 years. I believe the trust machine technology, which includes blockchain in its initial form, is a much more disruptive technology than the Internet, with more profound consequences to human society.
As regards research, we are building a new research team at Peking University. The area of research will be around the keywords like Cyberspace, Trust, Trust Machine, and new business models based on the new technology. I will touch upon a few points.
1. What is Cyberspace?
We all vaguely know what cyberspace is. However, it is not yet a precisely defined scientific concept. The time may have come that we gain a more formal understanding of it.
The first intuition of space comes from the 3-dimensional physical space, which can be extended to the 4-dimensional spacetimes. To describe the position of saying an airplane, you go to 5-dimensional space. To describe extended objects such as electromagnetic fields or the shape of an elastic body, you use function spaces which have infinite dimensions. All these types of spaces have the concept of continuity and various way of measurement in terms of distance, length, areas, and so on. In mathematics, another important type of space arises from the study of algebraic geometry and number theory, in which there can be found another type of continuity, as well as the various concepts of intersection between geometric configurations.
But what is cyberspace? From a simplistic view, you can think of it as a collection of computer systems connected by a certain communication network in which many parties can interact with each other. But this description hardly indicates its highly non-trivial complexity. The real wonder of cyberspace emerges only with the deep study of cryptography, as roughly described in what we earlier described as Trust 1.0–4.0. These are all based on some very profound mathematical principle, the existence of one-way function, which implies the famous conjecture P≠NP.
So, we see that cyberspace, namely the space of information, is really a quite strange animal. It is starkly different from any mathematical space we have encountered before. Its most important properties are derived from various non-invertibility of computation. To put it more quantitatively, it is about some asymmetry property of the computational process, measured by computational complexity. The times lock puzzle which later developed into the idea of verifiable delay function (VDF) shows this quantitative aspect more clearly.
Another question is, is cyberspace a purely discrete object? So far, the science of cryptography has mostly been approached by a discrete view. However, much important information contained in the form of voice, image and video are inherently more of continuous objects, which cannot be fully modeled by a discrete view.
So, is there a certain mathematical formulation of the concept of cyberspace, which can capture many of its important features, and serve as a foundation for future study?
2. Two Wings of Trust in Duality
We have informally discussed trust and its two aspects: 1) proper behavior enforcement; 2) privacy. They set limits on what you can do, and what you can see respectively. This reminds us of an important phenomenon in control theory, the duality between observability and controllability. This duality principle was first discovered in linear control theory, mathematically expressed by matrix transposition. Interestingly, this duality is also found in non-linear control theory based on differential equations, and in automata theory. So, is there a similar duality in the context of cryptography?
We have described blockchain as a half trust machine in the sense that it only limits what you do, but not what you see. In the general theory of MPC, we encounter another type of “half trust machine” which is secure only under “semi-honest” assumption, namely that each party will voluntarily do only what they are supposed to do (but may try their best to know what they are not supposed to know). These two types of “half trust machines” are apparently in some kind of duality. Interestingly, in both cases, the weakness can be fixed by zero-knowledge proof.
transparent blockchain + ZKP → blockchain of privacy
semi-honest secure MPC + ZKP → malicious secure MPC

Figure 14: How ZKP Relationship to Privacy-Preserving Computation and Malicious Secure MPC
We all know the wonder of the duality principle in mathematics. Starting with the duality between points and lines discovered in the early days of projective geometry, and later duality in the topology of manifold discovered by Poincare. Fourier transform is a kind of duality. There is also duality in optimization theory, linear programming, and so on. We have also heard about the duality which connects five different string theories into one M-theory. So, regarding the apparent duality we observed between the two aspects of trust, is it the result of some precise mathematical principle? Is there some kind of duality theory in cyberspace?
3. Trust Machine Construction
The quick rise of blockchain since 2009 has captured the eyes of the world. However, I personally feel that blockchain is but the “toy car” version of the much wider framework of Trust Machine Technology, which will be the real future.
From the point of view of business application (or more general social application), the real need is a trust machine, of which blockchain is a remote approximation. Blockchain is something you can play with immediately for quick results. But from a research point of view, you need to look a bit more ahead and probe further into the fundamentals.
Nowadays, there is a proliferation of experiments in this field, with vanilla blockchain, blockchain + ZKP, blockchain + storage, blockchain + data, blockchain +MPC, layer 2 solutions, cross-chain solutions, blockchain + TEE, and so on. All these are attempts to construct various forms of trust machine, using blockchain as a handy component.
But there could be a different approach to the problem. The all-powerful trust machine from MPC has already solved nearly all problems in theory. The next step is to look for concrete constructions which strike a reasonable balance among functionality, efficiency, security, and other practical factors. For this purpose, it seems necessary to develop more precise and quantitative measures to these different factors, so that we can better evaluate the merits of any specific construction. We can also ask whether a particular construction is optimal under certain conditions.
Given the above general view, we might also ask, what is blockchain as a trust machine? What is its place in trust machine construction in general? Should it occupy a central position, and if so, why? If not so, what are the other important tools? We see formal modeling of blockchain given in a 2015 paper on Hawk, which has such flavor.
Another very important question is the composition of trust machines. As discussed earlier, all separate trust machines constructed for a certain domain application in the world should eventually merge into one Global Trust Infrastructure. Is this technically viable? How should it be done? Experiments on cross-chain solutions are trying to address this issue from an engineering point of view. However, it seems unlikely that this very complex problem can find its proper solution by such a trial and error approach alone. Some true innovations based on advanced cryptography seem needed.
4. New Business Models
Trust machine in its ideal capacity (a highly efficient Global Trust Infrastructure) will render most of the traditional business model obsolete. However, present-day technology is not quite there yet. So, we expect a gradual process of evolution, with continuous technical and business innovation going hand in hand.
Bitcoin has been a most successful case of such a double innovation. Note that the technology is highly original, yet of very low capacity. So, one needs to dig into various vertical domains and identify the right kind of use cases. Such cases should have two characteristics: 1) business-wise, it should be disruptive and highly impactful to its relevant domain; 2) technically, it should be within the capacity of today’s technical innovation.
Question 9
Xinyu Tian:
In your presentation at the World Blockchain Congress 2021 in Hangzhou, you mentioned that the Internet Computer launched by DFINITY is one of the major breakthroughs in the mainstream of blockchain innovation in the past 10 years. How do you think the Internet Computer can possibly empower your research? What support do you need to innovate with the Internet Computer? What technical questions may you have for the DFINITY engineers? Are you interested in a collaboration between DFINITY and your research center?
Figure 15: DFINITY
Prof. Kevin Mo:
In our conversation today, what I consider the most important is the formation of a Global Trust Infrastructure, serving as the foundation of the whole future cyber economy and cyber social governance. Among all the blockchain projects I have come to know, DFINITY’s vision of the Internet Computer seems to come the closest to that idea of infrastructure. So, personally, I really like it very much and wish for its success.
In principle, any blockchain with smart contract capacity, such as Ethereum, Algorand, and so on, has the flavor of infrastructure, a kind of open operating system on the Internet. But to really function as such, major technical progress is still needed. A practically useful infrastructure must have unlimited scalability in computation, communication, and storage capacity, and the ability to protect the privacy of both data and codes when required. It’s like building a decentralized operating system on Internet, which is obviously a big and difficult job.
It’s wonderful to see DFINITY is making great progress in this general direction. At this point, I don’t know enough details about the actual technology of DFINITY yet. So, I am not able to make a very technical assessment. Hope I will be able to learn more about it in some future time and to appreciate its achievements more intimately.
I am certainly interested in the possible collaboration between DFINITY and our center. One possibility is to take Internet Computer as a ready framework for experimentation, to see how it may be used to foster highly innovative business models in some vertical domains. I have read about DFINITY’s ideas on decentralized TikTok, and even decentralized Android, which is all very inspiring. I believe there are many such possibilities waiting for our exploration.
Another possible contact point is our interest in the study of trust machine construction as discussed earlier. DFINITY itself is a great case of such construction. DFINITY working with other chains provide great cases for trust machine compositions. I personally feel that this is a vast fertile land for technical innovation. I would be quite glad to be engaged in some joint exploration in these directions.
Concluding Remarks
Prof. Luyao Zhang:
Thank you so much, Prof. Kevin Mo for your very insightful discussion today, and we will also contact DFINITY engineers for your questions like what is the technical thing that they think they can fulfill trust infrastructure for Web 3.0, and we will also get back to you about the answers of how we can develop future applications as students, scholars, and professors on this type of infrastructures.
Prof. Kevin Mo:
Thank you, Professor Zhang, for arranging this interview, and thanks to your team for all the preparation work. I am thrilled to have had this great discussion!
Relevant Materials
- Newtonian mechanics (Classical mechanics)
Newtonian/Classical mechanics is a physical theory describing the motion of macroscopic objects, from projectiles to parts of machinery, and astronomical objects, such as spacecraft, planets, stars, and galaxies.
2. Einstein’s relativity
The theory of relativity usually encompasses two interrelated theories by Albert Einstein: special relativity and general relativity, proposed and published in 1905 and
1915, respectively. Special relativity applies to all physical phenomena in the absence of gravity. General relativity explains the law of gravitation and its relation to other forces of nature. It applies to the cosmological and astrophysical realm, including astronomy.
3. Quantum physics
Quantum physics is the study of matter and energy at its most fundamental level. A central tenet of quantum physics is that energy comes in indivisible packets called quanta. Quanta behave very differently to macroscopic matter: particles can behave like waves, and waves behave as though they are particles.
4. Zero-knowledge proof
In cryptography, a zero-knowledge proof or zero-knowledge protocol is a method by which one party (the prover) can prove to another party (the verifier) that they know a value x, conveying no information apart from the fact that they know the value x. The essence of zero-knowledge proof is that it is trivial to prove that one possesses knowledge of certain information by simply revealing it; the challenge is to prove such possession without revealing the information itself or any additional information.
5. Homomorphic encryption
Homomorphic encryption is encryption that permits users to perform computations on its encrypted data without first decrypting it. These resulting computations are left in an encrypted form which, when decrypted, resulting in an identical output to that produced had the operations been performed on the unencrypted data. Homomorphic encryption can be used for privacy-preserving outsourced storage and computation. This allows data to be encrypted and out-sourced to commercial cloud environments for processing, all while encrypted.
6. Secure multi-party computation
Secure multi-party computation (also known as secure computation, multi-party computation (MPC), or privacy-preserving computation) is a subfield of cryptography with the goal of creating methods for parties to jointly compute a function over their inputs while keeping those inputs private. Unlike traditional cryptographic tasks, where cryptography ensures security and integrity of communication or storage and the adversary is outside the system of participants (an eavesdropper on the sender and receiver), the cryptography in this model protects participants’ privacy from each other.
7. Cyberspace
Cyberspace is a concept describing a widespread interconnected digital technology. It refers to the online world as a world ‘apart’, as distinct from everyday reality. The term is described as the domain of the global technology environment, commonly defined as standing for the global network of interdependent information technology infrastructures, telecommunications networks, and computer processing systems.
8. PKI/HTTPS technology
PKI: A public key infrastructure (PKI) is a set of roles, policies, hardware, software, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities, such as e-commerce, internet banking, and confidential email. It is required for activities where simple passwords are an inadequate authentication method and the more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred.
HTTPS: Hypertext Transfer Protocol Secure (HTTPS) extends the Hypertext Transfer Protocol (HTTP). It is used for secure communication over a computer network and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL). The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL.
9. Julius Caesar
Julius Caesar was a renowned general, politician, and scholar in ancient Rome who conquered the vast region of Gaul and helped initiate the end of the Roman Republic when he became dictator of the Roman Empire. Despite his brilliant military prowess, his political skills, and his popularity with Rome’s lower- and middle-class, his rule was cut short when opponents — threatened by his rising power — brutally assassinated him.
10. SSL/TLS
Transport Layer Security (TLS), the successor of the now-deprecated Secure Sockets Layer (SSL), is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use as the Security layer in HTTPS remains the most publicly visible.
11. Trusted third party (TTP)
In cryptography, a trusted third party (TTP) is an entity that facilitates interactions between two parties who both trust the third party; the Third Party reviews all critical transaction communications between the parties, based on the ease of creating fraudulent digital content. In TTP models, the relying parties use this trust to secure their own interactions. TTPs are common in any number of commercial transactions and in cryptographic digital transactions as well as cryptographic protocols. For example, a certificate authority (CA) would issue a digital certificate to one of the two parties in the next example. The CA then becomes the Trusted-Third-Party to that certificate’s issuance. Likewise, transactions that need third-party recordation would also need a third-party repository service of some kind or another.
12. John 20:29
John 20:29 is the twenty-ninth verse of the twentieth chapter of the Gospel of John in the New Testament. It records Jesus’ reappearance to the disciples, including Thomas, eight days after his resurrection.
Wikipedia
13. Proof-of-Work (PoW)
Proof-of-Work (PoW) describes a system that requires a not-insignificant but feasible amount of effort in order to deter frivolous or malicious uses of computing power, such as sending spam emails or launching a denial of service attacks.
14. Proof-of-Stake (PoS)
The Proof of Stake (PoS) concept states that a person can mine or validate block transactions according to how many coins they hold. This means that the more coins owned by a miner, the more mining power they have.
15. Proof-of-storage (PoS)
Proof-of-storage (PoS) is a cryptographic protocol used primarily to verify the integrity of a remote file. This is done by sending an encoded copy of the data to a server and then executing a challenge-response protocol to check the data’s integrity. This protocol is normally used when considering the efficiency of a cloud storage server.
16. TEE
A trusted execution environment (TEE) is a secure area of the main processor. It guarantees code and data loaded inside to be protected regarding confidentiality and integrity. A TEE as an isolated execution environment provides security features such as isolated execution, the integrity of applications executing with the TEE, along confidentiality of their assets. In general terms, the TEE offers an execution space that provides a higher level of security for trusted applications running on the device than a rich operating system (OS) and more functionality than a ‘secure element’ (SE).
Acknowledgments:
Interviewee: Prof. Kevin Mo
Interviewer: Tianyu Wu, Xinyu Tian, Prof. Luyao Zhang
Executive Editors: Tianyu Wu, Xinyu Tian
Advisor and Chief Editor: Prof. Luyao Zhang